Keeping Oxford secure: what we can all do to protect the University from cyber threats
Graham Ingram, Chief Information Security Officer, talks about Oxford's cybersecurity and what systems have been put in place to help protect the University

Did you know that the University sustained four times the number of cyberattacks in early 2020 compared to 2019? Do you know what systems have been put in place since?
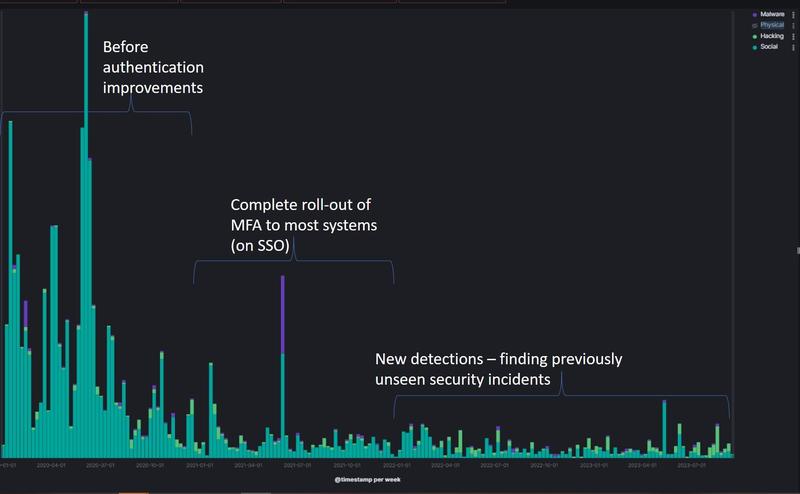
As Oxford’s Chief Information Security Officer (CISO), I am responsible for the security of our personal, research and business data. Some of the attacks we detected in 2020 were intercepted by new emergency measures put in place to protect specific systems supporting the Oxford–AstraZeneca vaccine and therapeutics research, such as Multi-Factor Authentication (MFA). Others were caught by existing University systems, such as Sophos. The volume and complexity of the cybersecurity incidents during our vaccine research made us rethink how we, as an institution, can prevent the potential catastrophic loss of clinical trials data integrity. The loss of this data would require re-running clinical trials and, ultimately, prevent the University from carrying out world-class research in a competitive market. It is a matter of when, not if, the next major cyber incident will happen.
During this period, it was not lost on the Information Security (InfoSec) team – the defenders of University data – that they ‘had to be constantly vigilant and legitimately defend the entire attacker surface, while the attacker only needs to succeed once at a single location'. (Huang, Huang & Zhu)1.
Whether we work directly with research data or not, we must all learn from this experience to accelerate the InfoSec programme. This blog describes a little of what we have achieved so far and, in conjunction with Digital Transformation, what you and I can do to make the University more secure.
What has been achieved over the last few years?
- Full roll-out of MFA to nearly 70,000 accounts. So far in 2023, our rate of confirmed cyber incidents is 9.5% of those over the same period in 20202. Cyber threat activity has continued to ebb and flow over the last few years, but we can still credit MFA with preventing many cyber attempts from evolving into serious incidents. This project from Michaelmas term 2020 to Hilary term 2021 set an HE sector-wide example of successful delivery during difficult times.
- Increased cooperation with government, industry and JISC – the higher education providers of the Joint Academic NETwork (JANET).
- Improvement of our ability to monitor the now-increased interconnect to JANET. We are one of the very few universities operating a 100GB pipe. I don’t know of any others monitoring the entirety of this for cyber intrusions as we are.
- Migrated on to an updated email security product to reduce the risk of one of the most prevalent cyber vectors. This system scans our inbound email for credibility and security. Up to 80% can be rejected as spam or phishing. Some of the rejected emails are emails carrying toxic attachments. The payloads in these rejected attachments include several attempts to deliver ransomware every day.
- Started a series of exercises to test our incident response and business continuity plans. At the University level, Silver and Gold incident response groups have conducted exercises. Various groups in IT services have run cyber incident response rehearsals as have many departments and colleges. Most others have plans to do similar events in the next term.
- Improved awareness throughout the University and the colleges. Increasing support for InfoSec has actively reduced the number of incidents being dealt with.
What is happening now and next?
With the support of many across the collegiate University, the InfoSec programme will focus on:
- The Oxford Secure project, which will equip staff and students with knowledge, life skills and resources related to cybersecurity and data privacy, so they can act as a joined-up human firewall to safeguard Oxford’s uniqueness. A new cybersecurity and data privacy training programme will be rolled out from Michaelmas term 2023, accompanied by an ongoing communications campaign to keep cybersecurity at the front of people’s minds.
- The Email Security and Simplification Project, which will reduce the risk of a breach of personal data and drive compliance with internationally recognised standards.
- A partnership between the Information Security Programme and Digital Transformation to ensure that we can seize all the opportunities of digitisation. To make this happen we will launch new services that assist in the discovery of information assets, expand our ability to analyse logs from local networks, and enhance that information and provide it back to local IT teams. We also have an aspiration to bring the collegiate baseline to ISO27001, the leading international standard for information security, and capture this on a digital risk platform.
- On the morning of 3 November, InfoSec will be hosting its first post-pandemic Cybersecurity Special Interest Group (CSIG) Threat Update since 2020. CSIG is a termly event where InfoSec briefs the University on the recent threat updates and what systems and policies have been put in place to negate these. The team will be giving an update on the threats Oxford has faced and continues to face.
- The Cybersecurity Competency Centre which will generate a team of experts you can consult for cybersecurity support. Existing IT staff in departments, divisions, faculties and colleges will be offered intensive training to become part of a distributed Competency Centre led by myself and working with colleagues in IT Services and the Digital Transformation team. I am pleased to say the first cohort recently received their formal training for a Certificate in Information Security Management Principles (CISMP). Some have already begun to gain their accreditation from the British Computer Society in April 2023. Our next training session in September is already oversubscribed and we are hoping to have many more in 2024.
- Cyber Taskforce: building on the Cybersecurity Competency Centre and the work done by InfoSec and IT Services during the vaccine development and rollout, a Cyber Taskforce is in the initial stages of creation. The taskforce will be a group of staff across the collegiate University who are familiar with cybersecurity tools and techniques. These members of staff will be on hand to support any Oxford user in the event of a cyber attack: when a major calamity hits the University, requiring all hands to the pump, these colleagues will work together to deliver much needed capacity and expertise.

What can you do?
At Oxford, I want to empower staff and their senior managers to take ownership of their own cybersecurity. From Research to Finance to Human Resources to Student Administration, each area will have their own unique risks they face in cybersecurity on a day-to-day basis.
Here are a few examples of what you can do to keep Oxford secure:
- Make sure you are up to date with your Information Security training.
- Be aware of the University’s best practice regarding Information Security.
- Familiarise yourself with the University’s Information Security Resources.
- Empower yourself and your staff with InfoSec’s personalised security training.
- Don’t be afraid to report a cybersecurity incident.
- Sign-up to our Competency Centre’s CISMP training.
- If you’ve completed your CISMP training and are interested in becoming part of the Cyber Taskforce, then get in touch.
- Get involved with the Digital Transformation Investigative Assignments. If you have a cybersecurity idea that could transform how the University does things, then get in touch with the team.
The Cybersecurity Competency Centre and Oxford Secure will be at the Professional Services Conference on 26 September at the Examinations Schools and at Oxford’s Digital Festival on 9 November at Jesus College, where our staff will be on hand to answer questions about what we’re doing and what our plans are for 2024.
If you are interested in getting involved in our Cybersecurity Competency Centre or our Cyber Taskforce, please get in touch.
[1] Yunhan Huang, Linan Huang, Quanyan Zhu, ‘Reinforcement Learning for feedback-enabled cyber resilience’, Annual Reviews in Control, Volume 53, 2022, pp273–295
[2] 1 Jan–12 Sep 2020 (before authentication improvements) = 2,091 confirmed incidents; 1 Jan–12 Sept 2023 = 199 confirmed incidents. But it only takes one incident to get out of control.